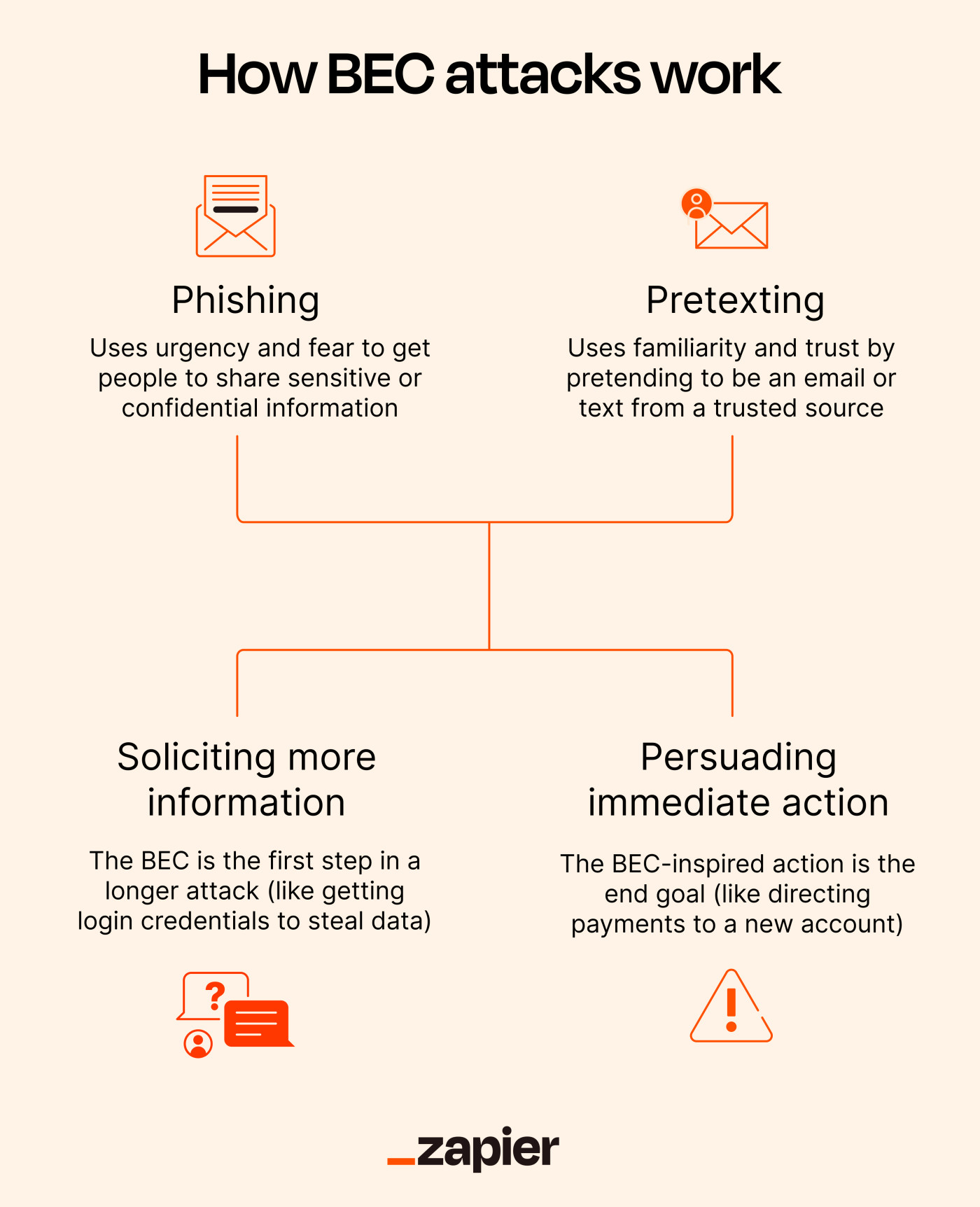
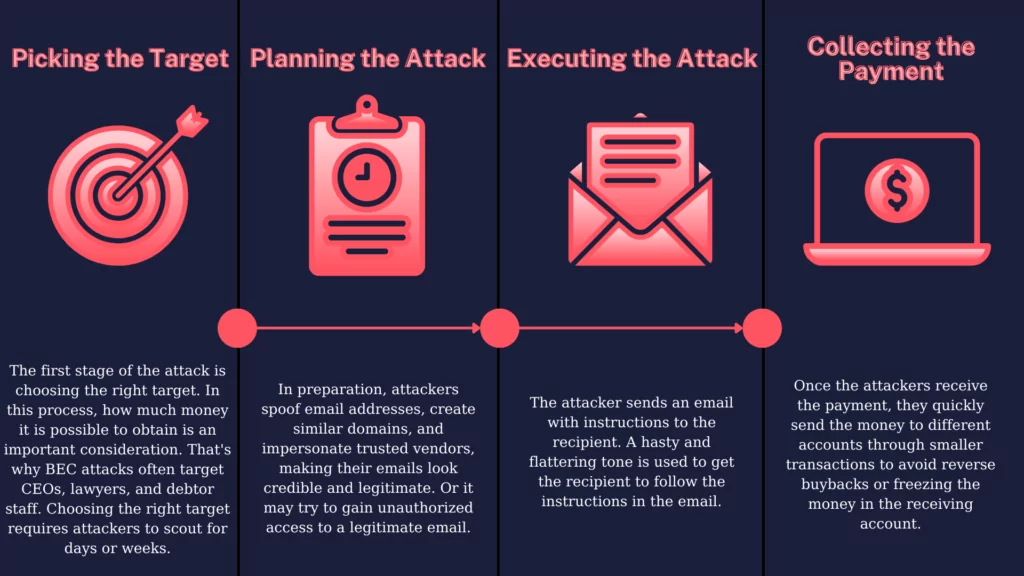
Behind the scenes of business email compromise: Using cross-domain threat data to disrupt a large BEC campaign | Microsoft Security Blog

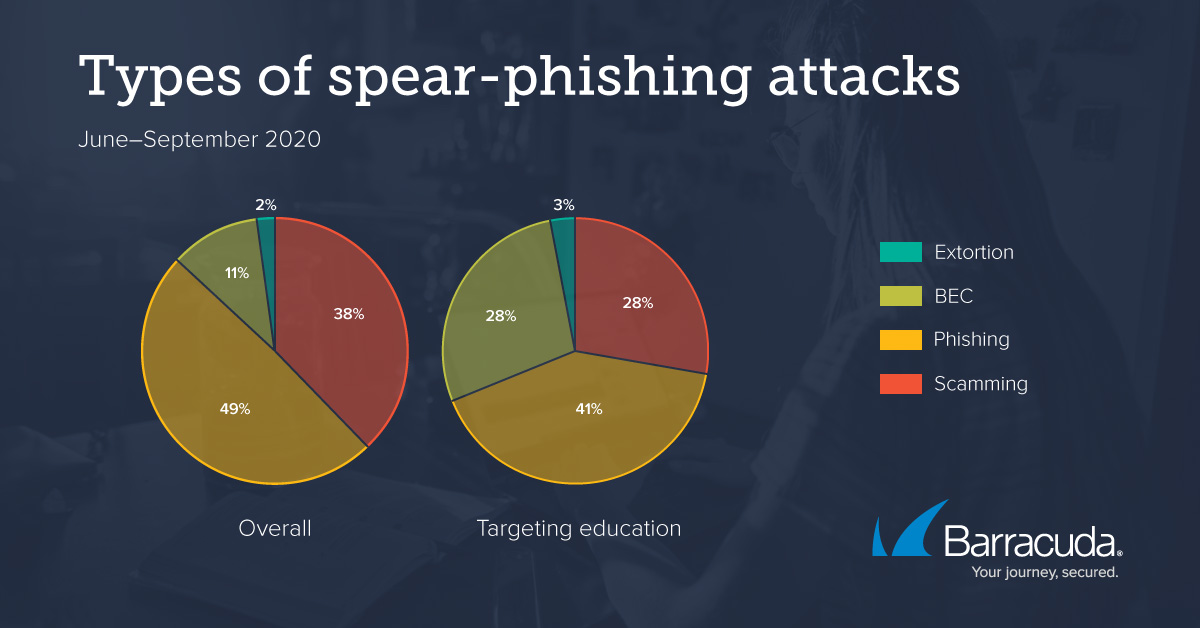
Armorblox Email Security Threat Report Reveals 72% Rise in Business Email Compromise Attacks in 2022 | Business Wire

Business Email Compromise: Unmasking the Tactics Behind CEO Fraud and Prevention Strategies - Security Investigation
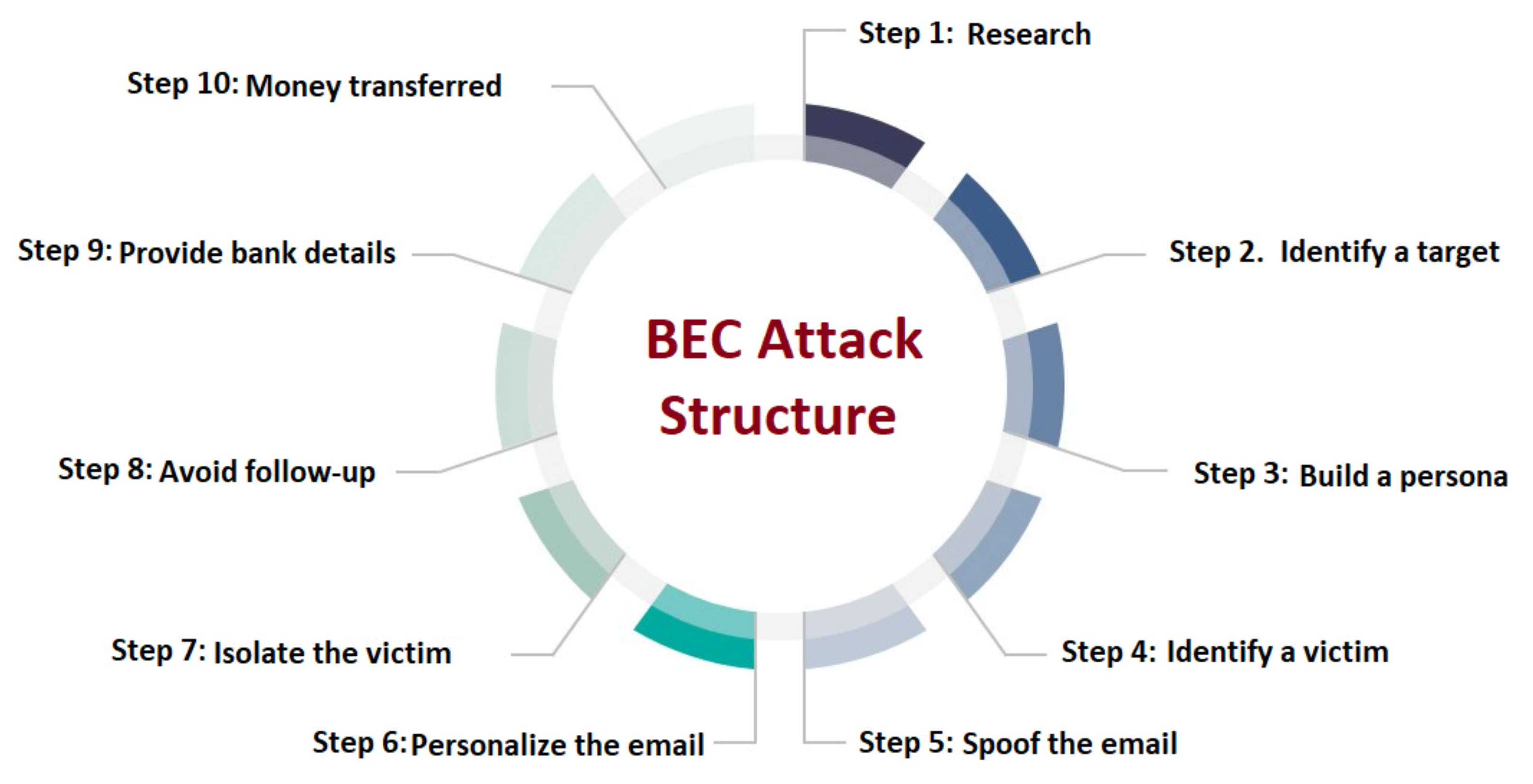
.png)