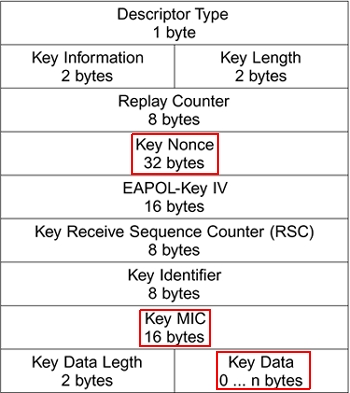
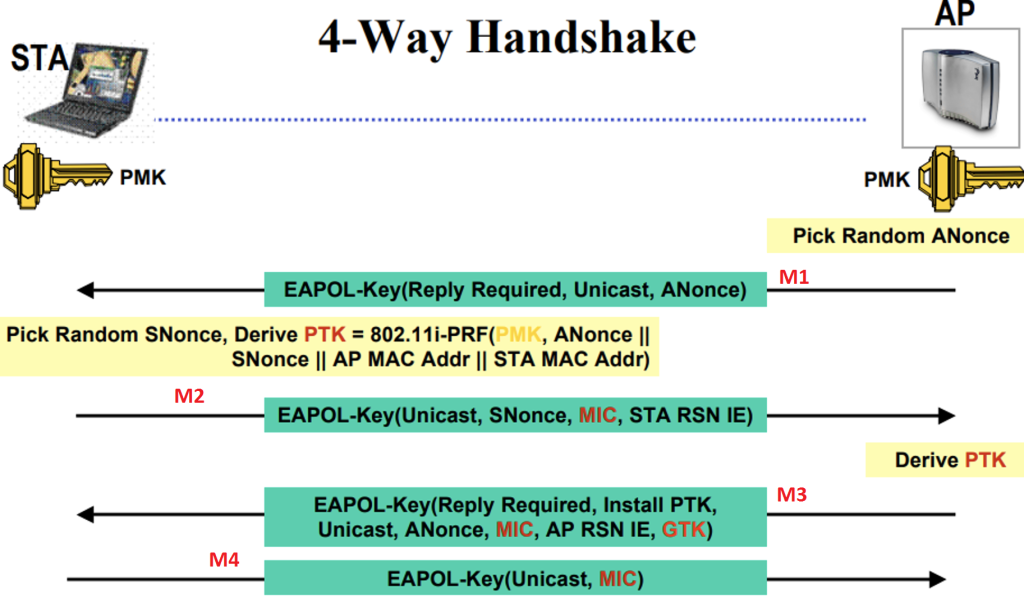
Figure 4 from Secure key exchange scheme for WPA/WPA2-PSK using public key cryptography | Semantic Scholar

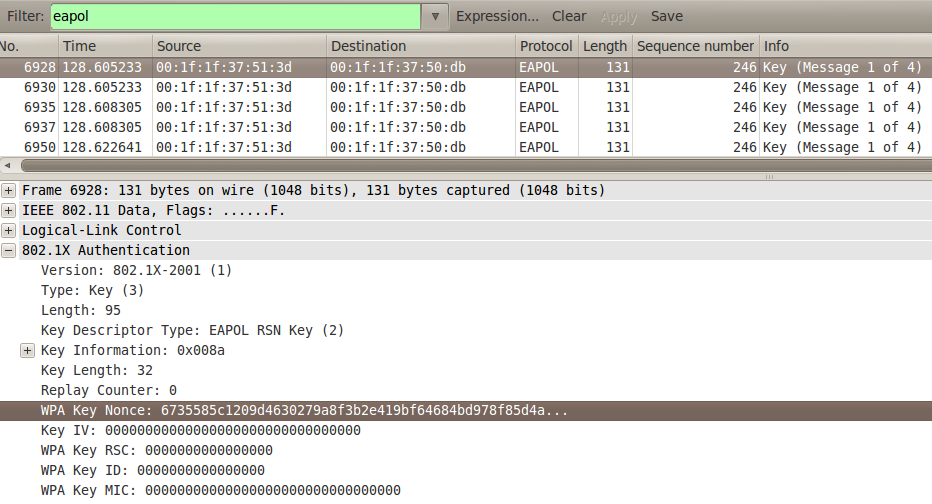
penetration test - can an attacker find WPA2 passphrase given WPA key data and WPA MIC - Information Security Stack Exchange

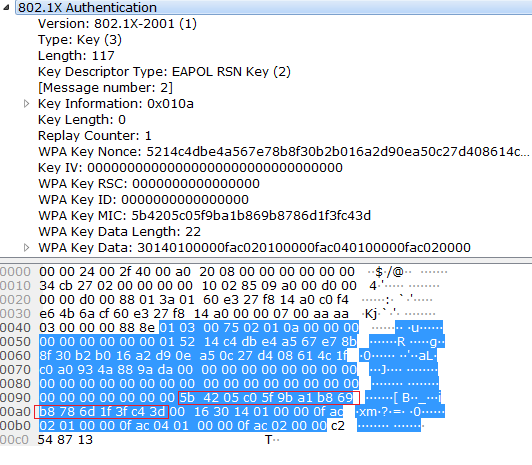
WPA-2 encryption and integrity check Message integrity check (MIC): AES... | Download Scientific Diagram

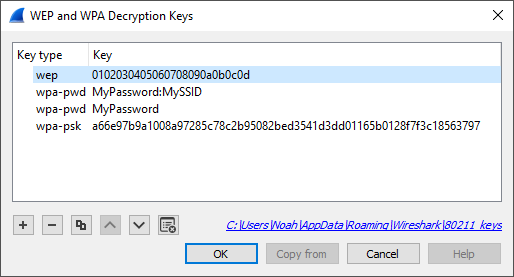



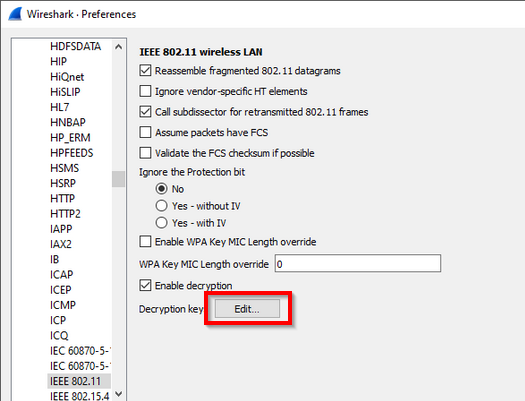
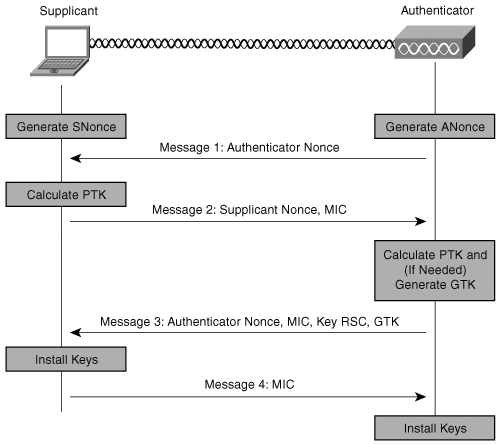

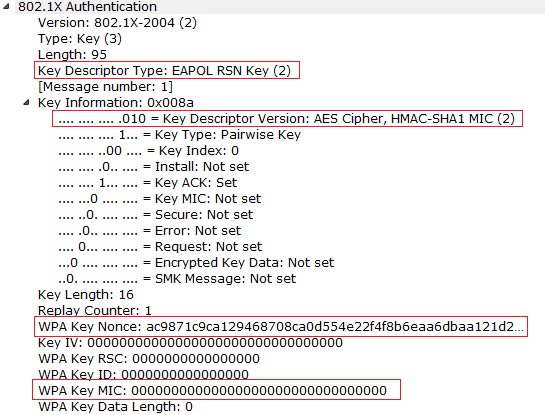
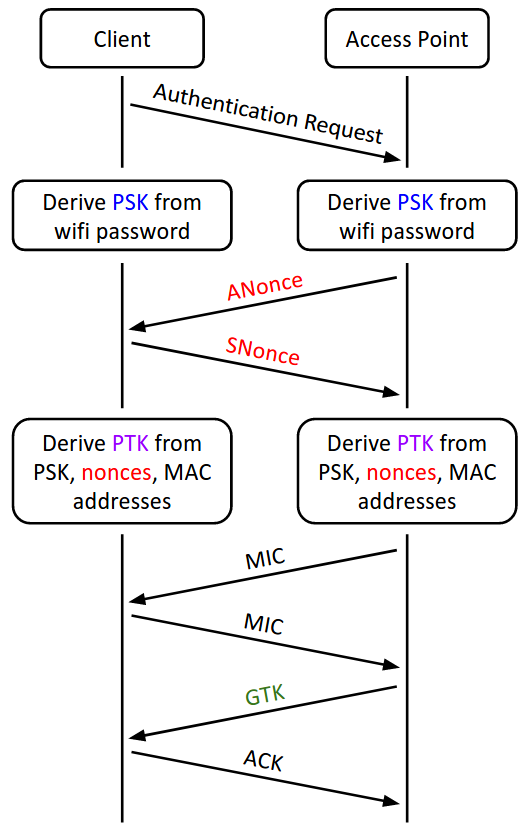


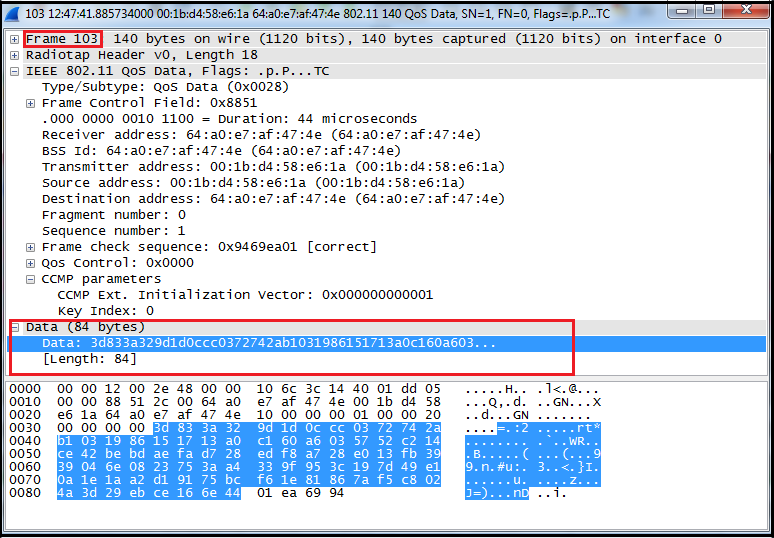
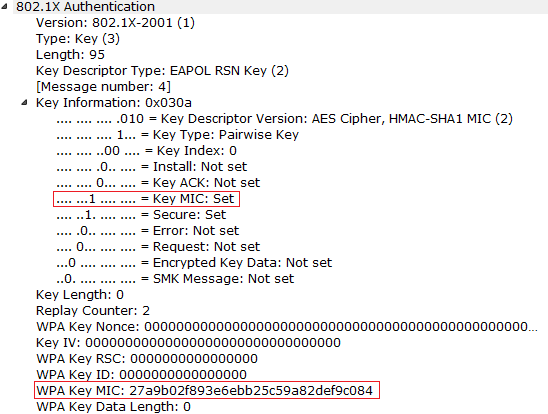
![Capturing WPA/WPA2 Handshake | Cracking Principles [CYBERPUNK ] Capturing WPA/WPA2 Handshake | Cracking Principles [CYBERPUNK ]](https://cdn.cyberpunk.rs/wp-content/uploads/2019/06/Capturing_WPA_WPA2_Handshake_bg.jpg)